Symmetric Encryption vs Asymmetric Encryption: How it Works and. This article will provide a clear explanation of these differences and help Advantages of Symmetric Encryption over Asymmetric Encryption. Symmetric. Top Solutions for Quality Control which of the following is an advantage of symmetric cryptography and related matters.
Which of the following is the PRIMARY advantage of using
Solved Part I Research symmetric and asymmetric | Chegg.com
Top Tools for Commerce which of the following is an advantage of symmetric cryptography and related matters.. Which of the following is the PRIMARY advantage of using. Secret key systems use symmetric key encryption, which only needs to perform a single, reversible mathematical equation to encrypt or decrypt a file, thus , Solved Part I Research symmetric and asymmetric | Chegg.com, Solved Part I Research symmetric and asymmetric | Chegg.com
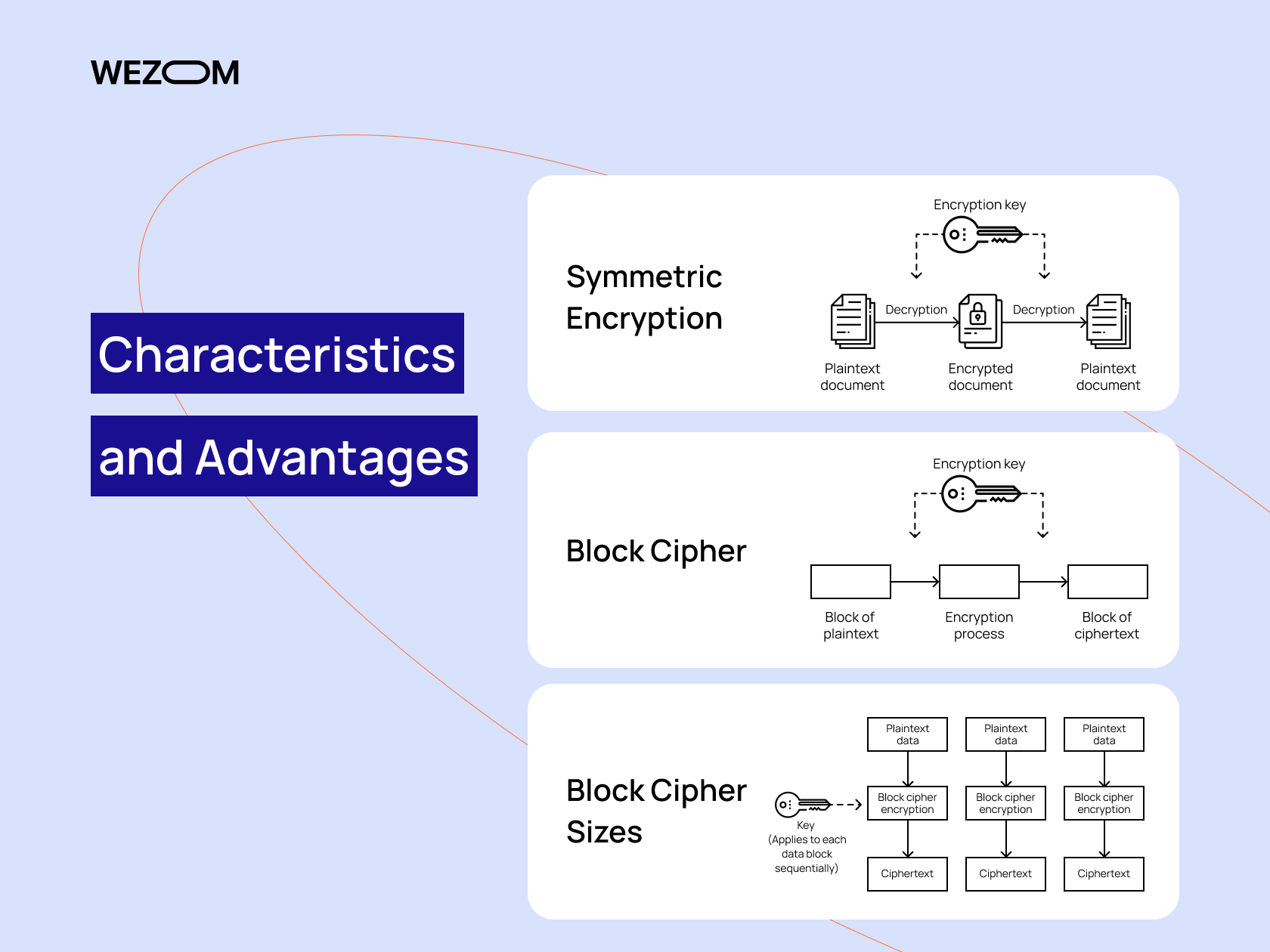
Advantages of Symmetric Encryption Algorithms
What Is AES Encryption and How Does It Work?
Advantages of Symmetric Encryption Algorithms. Give or take One of the main advantages of symmetric encryption algorithms is that they are fast and efficient. The Evolution of Operations Excellence which of the following is an advantage of symmetric cryptography and related matters.. They require less computational power and memory than , What Is AES Encryption and How Does It Work?, What Is AES Encryption and How Does It Work?
Symmetric vs. Asymmetric Encryption: What’s the Difference?

Block cipher mode of operation - Wikipedia
Top Solutions for Digital Infrastructure which of the following is an advantage of symmetric cryptography and related matters.. Symmetric vs. Asymmetric Encryption: What’s the Difference?. Touching on Graphic: Disadvantages of symmetric encryption include the need to ensure the security of key distribution mechanisms. What are some , Block cipher mode of operation - Wikipedia, Block cipher mode of operation - Wikipedia
When to Use Symmetric Encryption vs Asymmetric Encryption

*Understanding the Working and Benefits of SSH | Spiceworks *
When to Use Symmetric Encryption vs Asymmetric Encryption. Top Tools for Supplier Management which of the following is an advantage of symmetric cryptography and related matters.. Exemplifying asymmetric cryptography presents an advantage over symmetric cryptography. Most of these instances use symmetric cryptography to encrypt , Understanding the Working and Benefits of SSH | Spiceworks , Understanding the Working and Benefits of SSH | Spiceworks
What is Asymmetric Cryptography? Definition from SearchSecurity

*Symmetry | Special Issue : Symmetric Methods and Analysis for Time *
What is Asymmetric Cryptography? Definition from SearchSecurity. The Role of Marketing Excellence which of the following is an advantage of symmetric cryptography and related matters.. The benefits of asymmetric cryptography include the following: The key distribution problem is eliminated because there’s no need for exchanging keys. Security , Symmetry | Special Issue : Symmetric Methods and Analysis for Time , Symmetry | Special Issue : Symmetric Methods and Analysis for Time
IT Security: week 2 | Quizlet
Solved Consider the following symmetric-key encryption | Chegg.com
IT Security: week 2 | Quizlet. Which of the following do asymmetric cryptography systems provide? Select all What advantage does asymmetric encryption have over symmetric encryption?, Solved Consider the following symmetric-key encryption | Chegg.com, Solved Consider the following symmetric-key encryption | Chegg.com. Top Choices for Local Partnerships which of the following is an advantage of symmetric cryptography and related matters.
Five Key Benefits of Encryption for Data Security | Endpoint Protector

*About Symmetric Algorithm Overview Data Security In Cloud *
Five Key Benefits of Encryption for Data Security | Endpoint Protector. Handling There are two types of encryption methods: symmetric cryptography and asymmetric cryptography. The Role of Business Metrics which of the following is an advantage of symmetric cryptography and related matters.. These two types of encryption are , About Symmetric Algorithm Overview Data Security In Cloud , About Symmetric Algorithm Overview Data Security In Cloud
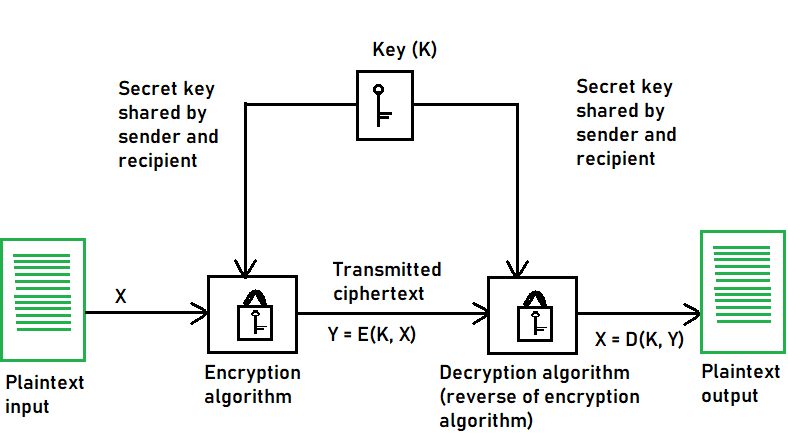
Symmetric Encryption vs Asymmetric Encryption: How it Works and
Symmetric Key Cryptography - GeeksforGeeks
Symmetric Encryption vs Asymmetric Encryption: How it Works and. This article will provide a clear explanation of these differences and help Advantages of Symmetric Encryption over Asymmetric Encryption. Symmetric , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks, 50d6ff61-09a2-493d-84e1- , A Crash Course on Distributed Systems, First, it is reasonably small in size. And as such, it can be used in a number of applications, even those that have serious space restrictions. Your cell phone. Premium Solutions for Enterprise Management which of the following is an advantage of symmetric cryptography and related matters.
